Dealing with NAT
| Introduction | This article describes the behavior of the NATDiscovery in the ByteBlower GUI. The text intends to answer technical questions. For a step-by-step guide on how to use NATDiscovery, we have an article in the examples section 📄 Use cases and examples. |
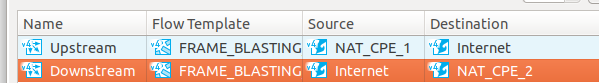
| Problem description | Any ByteBlower Port can be used as the source or destination of a FrameBlasting flow. As we'll see further, this makes an important difference. For clarity, we'll call traffic out of the NAT in the upstream direction. The ByteBlower Port with the NAT config is then the source of the flow. The reverse direction, traffic streaming into the NAT is called the downstream direction. In this second case, the NAT config is found on the destination. An example is found in the figure below. |
| Upstream discovery | As presented above, the addresses of packets from the CPE to the WAN are translated by the NAT. The upstream discovery determines the values they are being translated to. This discovery is done for FrameBlasting flows with a source that has the NAT config enabled. It's performed while setting up the test.
This forward discovery is done for all addresses. When multiple flows use the same frames and the same ports then the results of the forward discovery are reused. Most NAT devices will retain this translation for at least 2 minutes. Step 1: Frame creationA new frame is created based on the original frame. We'll call this the NAT Discovery Frame. It has the same values for the following fields:
The frame differs solely in the payload. This has been replaced with a small textual description and a unique token. It stays small: the frame is about 100 bytes including Ethernet overhead. Step 2: Upstream trafficThe probing frame is sent out from the ByteBlower port with the NAT config. The frame rate is low: about 10 packets a second or at about 8 kbit/s. Traffic is generated for at most 20 seconds, but as we'll see next, most of the time the NATDiscovery finishes earlier. Step 3 and 4: Receiving the frameA RawBasicCapture captures all traffic. A BPF filter based on the IPv4, and Layer 3 (mostly UDP) destination addresses of the frame limits the number of captured packets. Each received packet is compared to the expected payload from step 1. This comparison is done eagerly: as soon as new frames arrive. |
| Downstream discovery | In this section, we'll explain the downstream discovery. This algorithm is used when the destination of the FrameBlasting flow is behind a NAT.
Step 1 Do upstream discoveryUpstream discovery is started from the destination ByteBlower port, this is the ByteBlower port inside the NAT. This can be confusing: even though this port is configured to receive the traffic of the flow, it will transmit during initialization. Step 2: Adapt the FramesThe configured ByteBlower frames are modified to the learned NAT mapping. The public IPV4 address and learned Layer 4 port are used as the destination of the frame. |